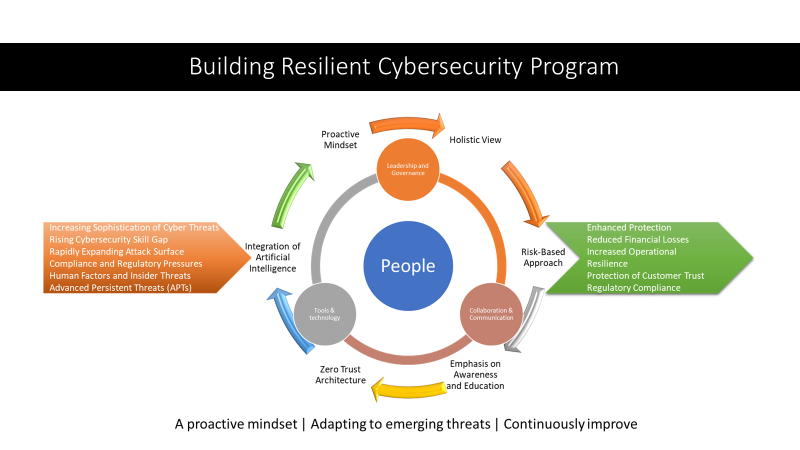
Introduction
Cybersecurity Ventures predicts global cybercrime costs will reach $10.5 trillion USD annually by 2025. As information security becomes an increasingly critical concern for organizations, the implementation of frameworks like KRITIS is becoming more and more necessary. KRITIS (Kritische Infrastrukturen) is a German framework for information security that sets out requirements for companies operating in critical infrastructure sectors, such as energy, healthcare, transportation, and finance. It provides a structured approach to risk management and information security, based on international standards such as ISO 27001, ISO 27002 and ISO 27009.

KRITIS implementation
Implementing KRITIS requires a systematic and structured approach. The first step is identifying critical assets, which are essential for the reliable and secure operation of the energy infrastructure. For instance, in electricity industry this would include power plants, transmission lines, substations, control centers, and other critical infrastructure components. Next, electricity companies must conduct a comprehensive risk assessment to identify potential threats and vulnerabilities to their critical assets. The risk management plan should outline the measures required to protect their critical assets, including technical and organizational measures to reduce the likelihood and impact of potential threats.
Once the risk management plan is in place, electricity companies must implement the security controls and measures outlined in the plan to protect their critical assets. This includes implementing technical measures such as firewalls, intrusion detection systems, and encryption, as well as organizational measures such as policies, procedures, and training programs. To ensure the effectiveness of the security measures, electricity companies must continuously monitor and assess their performance and conduct regular security assessments to identify new threats and vulnerabilities. They must also comply with relevant regulations and standards and report security incidents and breaches to the relevant authorities.
Artificial Intelligence in Information Security
The KRITIS framework is a comprehensive approach to securing critical infrastructure, but its implementation can be a daunting task. Fortunately, AI tools can help streamline the process and improve security outcomes. For example, AI tools can assist in conducting a comprehensive risk assessment to identify the specific risks and vulnerabilities that an organization faces. AI algorithms can analyze terabytes of data from multiple sources to identify and prioritize the most critical risks. This approach can be much more efficient and effective than traditional manual risk assessments.
AI tools can also help with the implementation of appropriate security controls to mitigate identified risks. For example, cybersecurity companies like Darktrace use AI algorithms to analyze network traffic in real-time and identify anomalous behavior that may indicate a cyberattack. Darktrace can also automatically implement security controls, such as blocking malicious traffic, to mitigate the risk. Similarly, AI tools can assist in managing compliance with the KRITIS framework and other information security regulations and standards. Cybersecurity companies like Tenable can scan an organization’s IT systems to identify vulnerabilities and compliance gaps and provide automated reports on compliance with the KRITIS framework and other security standards.
Conclusion
In conclusion, the implementation of the KRITIS framework is critical for organizations operating in critical infrastructure sectors, such as energy, healthcare, transportation, and finance, to protect their critical assets from cyber threats. The use of AI tools can assist organizations in streamlining the implementation process and improving security outcomes. However, organizations must also address the challenges of a shortage of skilled cybersecurity professionals and the constantly evolving threat landscape. As the KRITIS framework continues to evolve, it is important for organizations to stay informed and adapt their security strategies to keep pace with the changing threat landscape and incorporate emerging technologies and best practices.