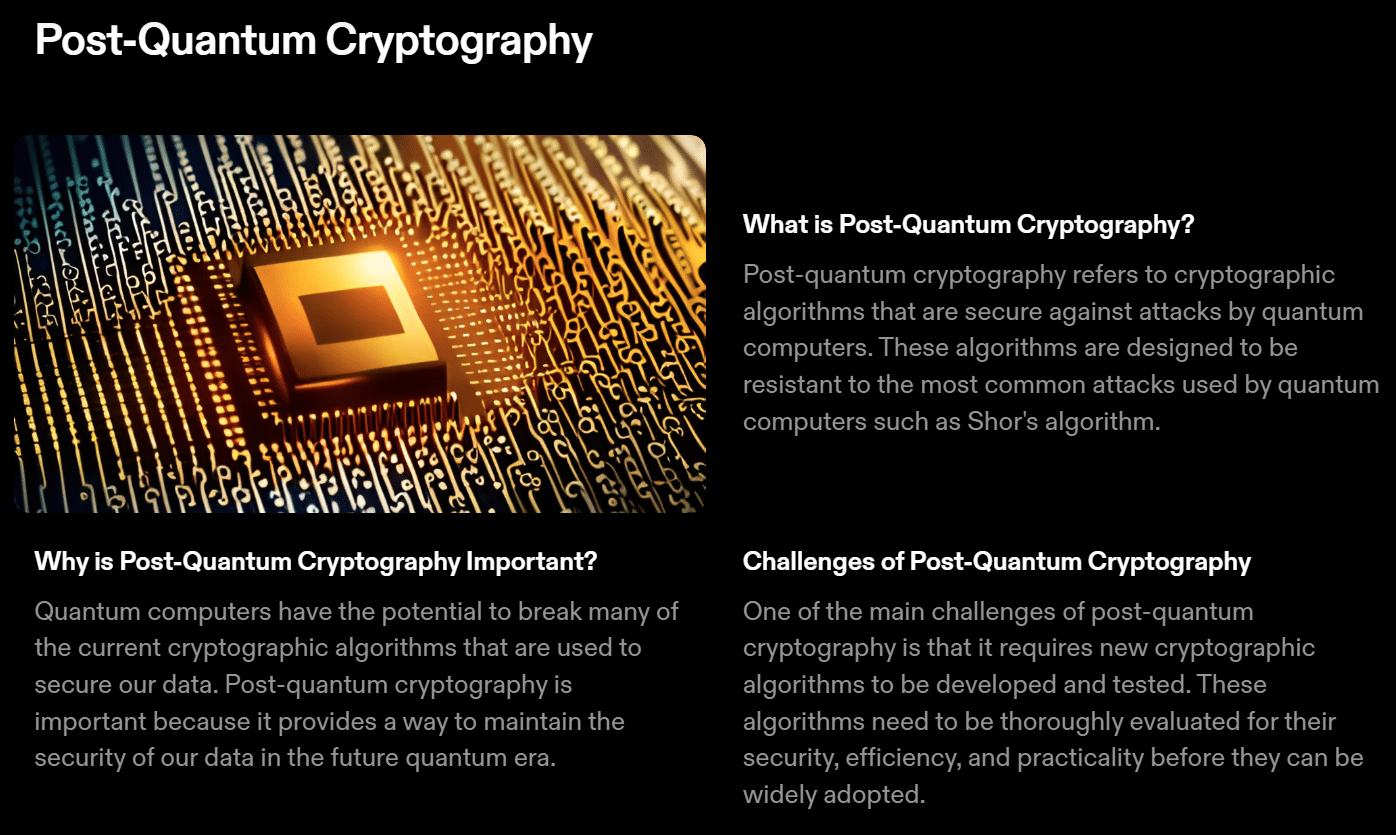
Quantum computing stands at the forefront of technological advancement, poised to reshape various industries, including cybersecurity. Its ability to perform lightning-fast calculations has the potential to challenge our current encryption methods and cyber defenses. Although quantum computing is still in its infancy, it’s crucial to proactively address the security risks it presents. In this article, we’ll explore who to strengthen your cybersecurity for the quantum era.
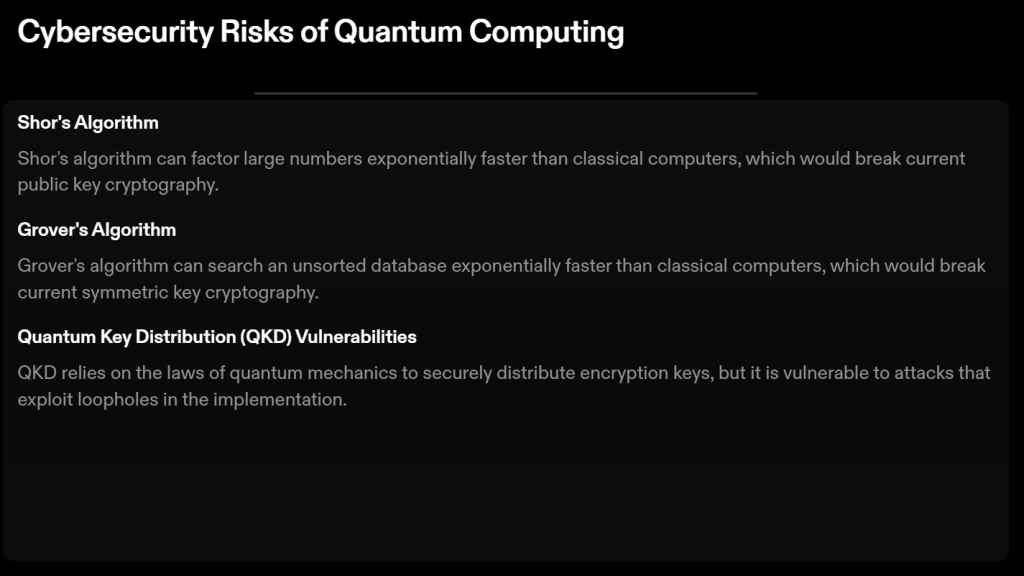
Identify Your Vulnerabilities:
The initial step in preparing for quantum computing threats is identifying your organization’s most vulnerable assets and systems. This includes pinpointing databases housing sensitive data, financial records, healthcare information, or systems that control critical infrastructure. Recognizing your weak points is fundamental to developing a robust defense.
Assess Your Risk:
After identifying critical assets, it’s essential to assess your risk. This involves evaluating the likelihood of a quantum computing attack and its potential impact. The likelihood depends on the availability of quantum computers and the skill level of potential attackers, while the impact is determined by the sensitivity of the compromised data or systems.
Develop a Mitigation Plan:
With risk assessment in place, crafting a comprehensive mitigation plan is the next logical step. This plan should incorporate a mix of technical and administrative controls. Technical controls encompass implementing quantum-safe cryptography, deploying multiple encryption algorithms, and regular key rotation. Administrative controls involve training employees in cybersecurity best practices and instituting security policies and procedures.
Stay Informed:
The landscape of quantum computing is continually evolving, making it crucial to stay informed about the latest developments. This awareness enables you to identify and counter new risks as they emerge.
Mitigation Strategies:
- Leverage Post-Quantum Cryptography: Embrace post-quantum cryptography, a cutting-edge field that develops cryptographic algorithms resistant to quantum attacks. Numerous algorithms in this category are under development and standardization.
- Adopt a Defense-in-Depth Approach: Layer multiple security controls to create a complex defense system. Combining encryption, authentication, access control, and other measures enhances the difficulty for attackers.
- Regular Data Backups: In the event of a successful breach, maintaining up-to-date data backups ensures quick recovery and minimal disruption to your operations.
- Proactive Monitoring: Implement continuous system and network monitoring for signs of suspicious activity. This allows for early detection and rapid response to potential threats.
By diligently applying these strategies, you can begin to fortify your cybersecurity for the quantum era. As technology advances, so too must our defense mechanisms to safeguard our digital future.